Which Methods Can Be Used to Implement Multifactor Authentication
Universal 2nd Factor U2F security keys physical one-time PIN OTP tokens. Prepare to Launch Multi-Factor Authentication.

5 Best Practices For Implementing Mfa To Reduce Resistance
You may have to make use of multiple level passwords for authentication.

. VPNs and VLANs IDS and IPS passwords and fingerprints tokens and hashes Explanation. SMS one-time passwords OTPs. Something you know typically a password.
The most common are. On your mobile app select add a new account. A cybersecurity specialist must be aware of the technologies available.
They currently offer at least two different multi-factor options. Some such preventive methods may include-. When prompted to register a verification method in this case Salesforce Authenticator click Choose Alternative Method.
Push Notifications with Auth0 Guardian. Location-based authentication is a special procedure to prove an individuals identity on. A major step in every multifactor authentication deployment is getting users registered to use Azure AD Multi-Factor Authentication.
A cybersecurity specialist must be aware of the technologies available. Multi-factor authentication often involves the use of passphrases in addition to one or more of the following multi-factor authentication methods. Multi-factor authentication methods you can add to your forms.
Azure AD Multi-Factor Authentication works by requiring two or more of the following authentication methods. The various ways to implement multifactor with Auth0 are as follows. Which methods can be used to implement multifactor authentication.
Which methods can be used to implement multifactor authentication. The list below reviews some common authentication methods used to secure modern systems. Something you are - biometrics like a fingerprint or face scan.
If you have implemented or want to implement Duo security as a third-party multi-factor authentication MFA solution and IAM manages your primary authentication and identity management you can connect to and integrate with Duo to secure Oracle IaaS PaaS or SaaS applications or to secure applications already secured by IAM. Passwords can be in the form of a string of letters numbers or special characters. Here we will explain some of the most popular authentication methods used in MFA and that you can easily implement in your Arengu flows without coding.
A cybersecurity specialist must be aware of the technologies available that support the CIA triad. 1 day agoWhat can I use to implement biometric authentication in an LDAP directory service. Multi factor authentication proves helpful in preventing your valuable data from being hacked or stolen.
Two Factor Authentication or 2FA is an advanced method of user authentication and a subset of multi-factor authentication mechanisms. How does location-based authentication work. You can query the location service running on a device which may be using GPS or Wi-Fi to triangulate its position and you can use a geolocation by IP database.
Guardian offers a frictionless approach to implementing MFA for your apps and. Passwords are the most common methods of authentication. Authentication methods such as Voice and SMS allow pre-registration while others like the Authenticator App require user interaction.
There are several methods for implementing multifactor authentication to your mobile app website or web app as part of your customer identity management system. Select Use Verification codes from an authenticator app. Authentication app which uses a free app on your smartphone from Authy Google Microsoft and many other vendors also offer one that generates the one-time PIN.
One excellent example of a multi-factor authentication supporting online service is that of PayPal. Which methods can be used to implement multifactor authentication. One option involves a credit card-sized device that produces on-demand a one-time-use six-digit.
2FA enhances the security of its user accounts by adding another layer of authenticity challenge after traditional passwords used in single-factor authentication. What methods can be used to implement location-based authentication. TOTP Time based Single One-Time Password usage.
Which methods can be used to implement multifactor authentication. A cybersecurity specialist must be aware of the technologies available that support the CIA triad. Concentrate on finding any networks or systems where deploying MFA will take more work for example if SAML authentication is used and especially on discovering vulnerable apps that dont support anything except passwords because they use legacy or basic authentication.
User attempts to login. 9 rows Which methods can be used to implement multifactor authentication. To add a Third-Party Authenticator ToTp app follow the steps below.
Which methods can be used to implement multifactor authentication. This includes older email systems using MAPI EWS IMAP4 POP3 SMTP. I dont mean the method retinal scans fingerprint readers etc but the type of authenticatiodnecessary.
Administrators must determine how users will register their methods. But if you can push onwards and implement one of the other methods you will be better protected. This prevents hackers from accessing any valuable information.
Something you have such as a trusted device thats not easily duplicated like a phone or hardware key. IDS and IPS tokens and hashes VPNs and VLANs passwords and fingerprints Explanation. Most online services and accounts offer true multi-factor authentication and the number is growing.
Any authentication method you can think of can be a part of a MFA system. Verification Methods for Multi-Factor Authentication. Recover MFA Access for products built on the Salesforce Platform Test MFA for B2C Commerce Cloud Test MFA for products built on the Salesforce Platform Get Customizable Templates With the MFA.
Auth0 supports sending an SMS with a one-time password code to be used for another step of verification.

4 Multi Factor Authentication Mfa Apis Nordic Apis
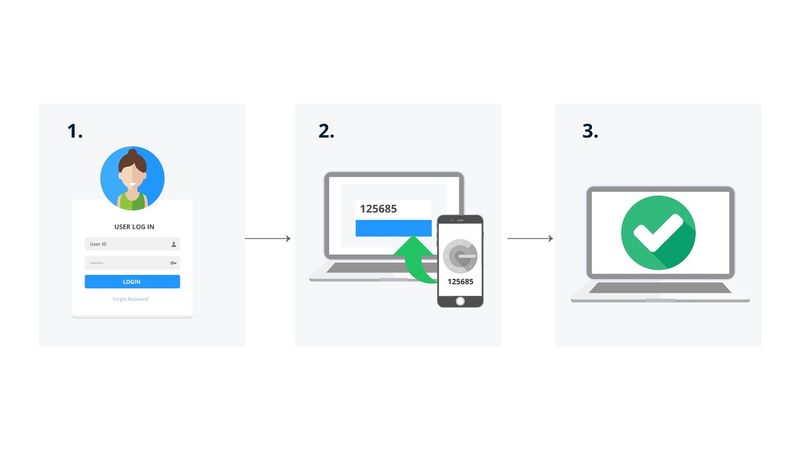
The Importance Of Multi Factor Authentication Mfa Loginradius Blog

Believe These 6 Mfa Myths At Your Own Risk In 2022 Security Solutions Business Data Myths

Multifactor Authentication Is Considered The Best Practice In Securing The Data Some Statistics Hig Types Of Crimes Multi Factor Authentication Identity Theft

Will Be Rescheduled Join Me At The Acapp Ap And P2p Leadership Conference May 27th Save 25 Leadership Conference Leadership Conference

Increased Use Of Multi Factor Authentication Mfa

Best Practices For Multi Factor Authentication Mfa Delinea

Approaches To Multi Factor Authentication Curity
Multi Factor Authentication Mfa Best Practices And Benefits

Asp Net Core Mvc File Upload Example Regular Expression Success Message Easy Spells
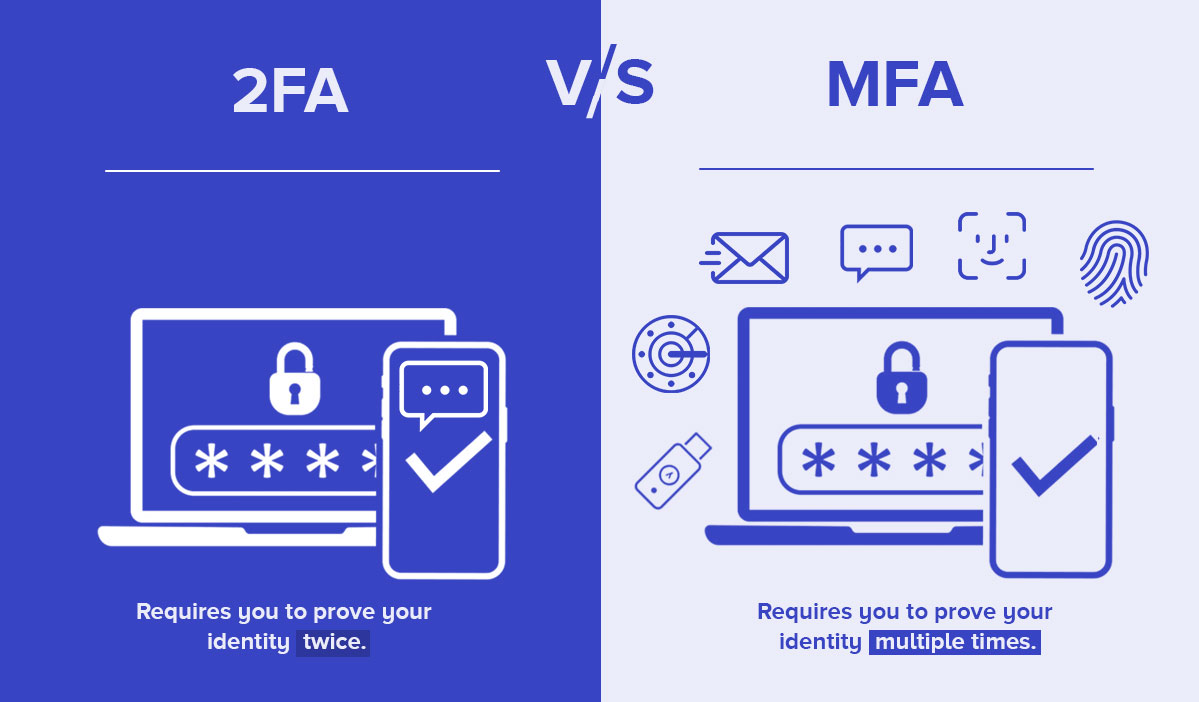
Two Factor Vs Multifactor Authentication What S The Difference Sso Single Sign On Solutions
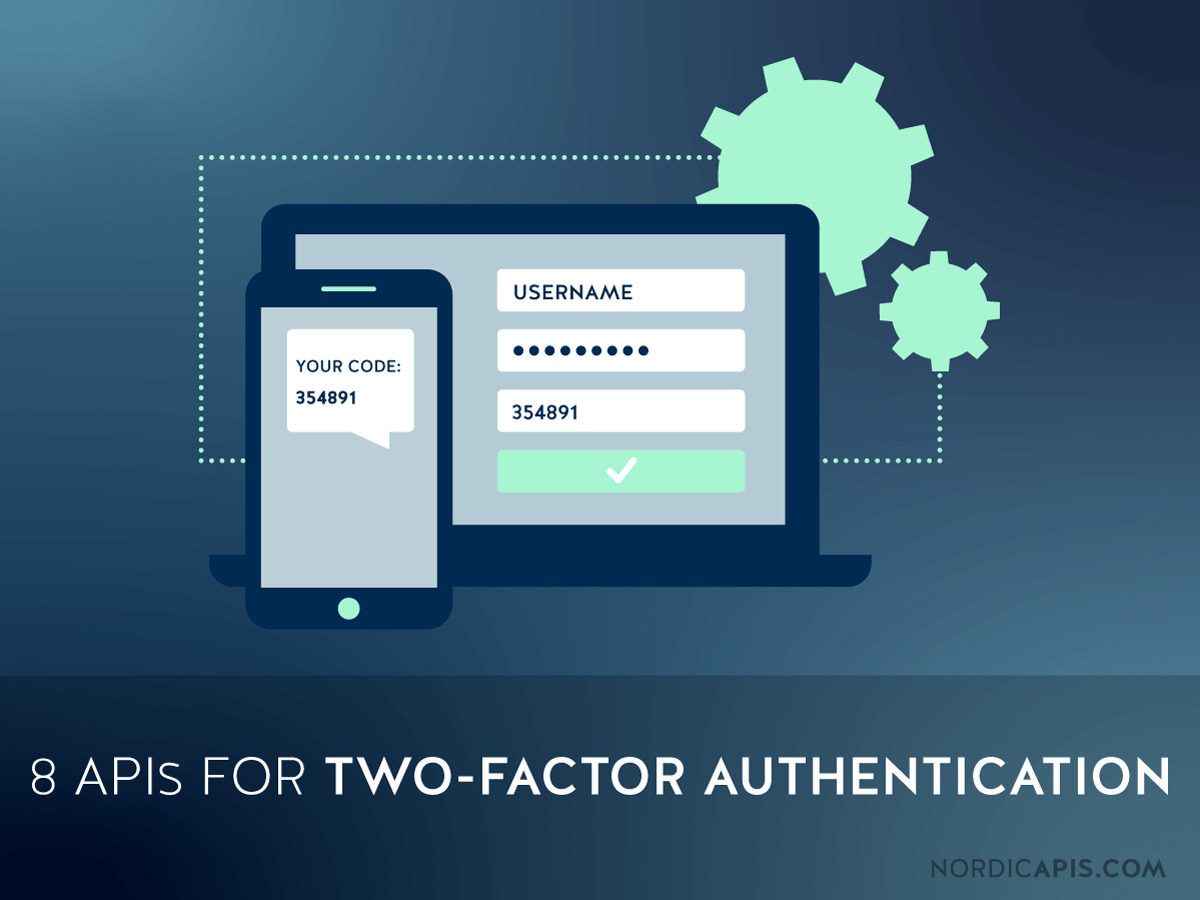
8 Apis For Two Factor Authentication Nordic Apis

Introduction To Multi Factor Authentication Curity

Email Marketing Plays An Inimitable Impression On The Potential Customers This Is The Easiest Way To Connect Web Development Design Web Design Website Design

5 Proven Ways To Improve Cyber Security For Your Business Cyber Security Password Protection Supportive

Google Always Gives A New Android Release A Dessert Name And A Matching Mascot Statue To Go With It Once Upon A Time There Was Muc Android Dessert Names Nuts
Two Factor Authentication 2fa Knowledge

Configure Identity Asp Net Core Identity Core Entity Framework

Comments
Post a Comment